SANTA BARBARA, CA—November 29, 2004
Green Hills Software, Inc., the market leader in safety-critical
and royalty-free Real-Time Operating Systems (RTOS), today announced
the immediate availability of INTEGRITY® PC, an extension
to the company’s INTEGRITY operating system that enables
the incorporation of legacy applications and traditional operating
systems, such as Linux, into high-security and high-reliability
applications.
|
 |
|
Boeing is using INTEGRITY PC to take advantage of existing Linux-based
software. With INTEGRITY PC, Boeing engineers did not have to port
their Linux code to a secure operating system and they can easily incorporate
updates to the Linux-based code.
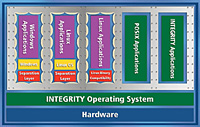
INTEGRITY PC integrates the INTEGRITY operating system with Green Hills
Software’s new Padded Cell™ secure virtualization technology.
The Padded Cell technology implements a “virtual computer” in
a user-mode application running on top of the INTEGRITY operating system.
Multiple Padded Cell applications can run concurrently on a single
physical computer, each hosting its own guest operating system. An
impenetrable wall around each virtual computer ensures that errant,
insecure or malicious code can never compromise the security or reliability
of the rest of the system—either inadvertently or via a hostile
attack.
“Like a padded cell, INTEGRITY PC prevents Linux, non-memory-protected
operating systems such as Wind River’s legacy VxWorks, and other insecure
and unreliable software from harming the rest of a system while also limiting
the harm it can do to itself,” explained Dan O’Dowd, founder and
chief executive officer of Green Hills Software. “For years, the INTEGRITY
operating system has lead the market for security-critical and safety-critical
applications, including leading-edge avionics and defense applications. Now,
with INTEGRITY PC, users of enterprise operating systems can upgrade to a secure
foundation without having to re-implement their existing applications. Legacy
operating systems and applications can safely co-exist with totally reliable
and security-critical applications running natively under the INTEGRITY operating
system.”
Key Features and Problems Solved
Key features and security threats addressed by INTEGRITY PC include:
- Guest operating systems and their applications run as “user
mode” INTEGRITY applications, which means that they cannot
alter the hardware’s configuration. This prohibits them from
circumventing the protections imposed by the INTEGRITY operating
system.
- Hardware memory protection prevents software running within a
virtual computer from reading or writing memory not explicitly
allocated to it. Even if a virtualized application were contaminated
by a buffer overrun exploit, hacker, virus, worm or Trojan horse,
it would not be able to corrupt, disrupt or spy on any other part
of the system. Moreover, a hacker cannot leverage a break-in of
software running in one virtual computer to gain access to the
rest of the system.
- All Input and Output (I/O) operations can be monitored, including
network communications. This allows aberrant activity, such as
that generated by spyware and hackers, to be detected and filtered.
Because the monitoring function is performed by a native INTEGRITY
application, it cannot be subverted or disabled by software running
under a guest operating system.
- Guaranteed resource availability provides each virtual computer
and native INTEGRITY application with the processor bandwidth and
memory required for successful execution. No software can exhaust
the resources needed by another application or by the INTEGRITY
operating system—thwarting any denial of service attack.
- Completely deterministic, real-time performance is provided by
the INTEGRITY operating system, enabling the co-existence of real-time
and general-purpose applications.
- Green Hills Software’s Integrate tool allows users to graphically
configure and visualize a system’s security, such as the
allocation of resources to an application, the devices that an
application can access, and which applications can communicate
with each other.
Flexible Interfaces
INTEGRITY PC supports the simultaneous use of multiple system interfaces,
for maximum developer and user flexibility:
- The use of one or more guest operating systems provides binary
compatibility with existing applications, no re-compilation is
needed. Multiple instances of the same or different operating systems
can run concurrently in different virtual computers, allowing programs
to be compartmentalized for increased security.
- POSIX interfaces provide source code portability with UNIX and
Linux applications together with the reliability and security benefits
of the INTEGRITY operating system. The INTEGRITY operating system
is the first and only operating system to be certified under the “POSIX®:
Certified by IEEE and The Open Group” program to the 1003.1™-2003
System Interfaces Product Standard and is listed on the certification
register at http://get.posixcertified.ieee.org/register.html.
- INTEGRITY interfaces offer full access to the operating system’s
underlying security and real-time performance capabilities.
Availability
INTEGRITY PC running on PowerPC processors with support for Linux
as a guest operating system is available today. Please contact
Green Hills Software for availability information for other target
processors and guest operating systems.
About Green Hills Software
Founded in 1982, Green Hills Software, Inc. is the technology leader
for real-time operating systems and software development tools for
32- and 64-bit embedded systems. Our royalty-free INTEGRITY RTOS, velOSity microkernel,
compilers, MULTI and AdaMULTI Integrated Development Environments
and TimeMachine debugger, offer a complete development solution that
addresses both deeply embedded and high-reliability applications.
Green Hills Software is headquartered in Santa Barbara, CA, with
European headquarters in the United Kingdom. Visit Green Hills Software
on the web at www.ghs.com.
North American Sales Contact:
Green Hills Software, Inc.
30 West Sola Street,
Santa Barbara, CA 93101,
Tel: 805-965-6044
Fax: 805-965-6343
Website: www.ghs.com
Email: sales@ghs.com
|
International Sales Contact:
Green Hills Software Ltd.
Fleming Business Centre
Leigh Road
Eastleigh
Hampshire SO50 9PD
UNITED KINGDOM
Tel: +44 (0)2380 649660
Fax: +44 (0)2380 649661
Email: mktg-europe@ghs.com
|
Media Contacts:
Green Hills Software, Inc.
Lynn J. Robinson
(805) 965-6044
lynnr@ghs.com |
|
|
|
|